Protect Your Devices the Smart Way in 2025: A Complete Guide for Business Owners
Protect Your Devices the Smart Way
Published: October 1, 2025 | Updated Quarterly | Reading Time: 18 minutes
In an era where cyberattacks occur every 39 seconds, and the average cost of a data breach has surged to $4.45 million in 2025, protecting your business devices is no longer optional—it’s critical for survival. For small business owners, where a single security incident can mean the difference between thriving and closing shop, understanding comprehensive device protection has become as fundamental as having insurance for your storefront.
The landscape of device protection has evolved dramatically. We’re no longer just talking about antivirus software and screen protectors. Today’s threat environment encompasses sophisticated ransomware attacks, AI-powered phishing schemes, supply chain vulnerabilities, and even quantum computing threats on the horizon. Meanwhile, the devices themselves have multiplied: smartphones, tablets, laptops, IoT sensors, point-of-sale systems, and cloud-connected equipment all require protection.
According to Gartner’s 2025 Security Spending Report, small and medium businesses are increasing their security budgets by 12.4% year-over-year, yet 60% still lack comprehensive device protection strategies. This guide will change that for your business.
🎯 TL;DR: Key Takeaways
- Layered Protection: Modern device security requires combining physical protection, cybersecurity measures, insurance coverage, and employee training into one cohesive strategy.
- Zero Trust is Essential: Implementing zero-trust architecture reduces breach risk by 45% according to recent studies, making it a critical 2025 standard.
- AI-Powered Threats: Cybercriminals now use AI for sophisticated attacks; your defenses must be equally intelligent with AI-driven security tools.
- Insurance Matters: Device insurance and cyber liability coverage can save businesses $50,000+ per incident, yet 70% of small businesses remain uninsured.
- Mobile-First Risk: With 85% of business activities now occurring on mobile devices, smartphone and tablet protection is paramount.
- Compliance Costs: Non-compliance with data protection regulations can result in fines up to 4% of annual revenue—prevention is significantly cheaper.
- Recovery Planning: Businesses with comprehensive backup and recovery plans resume operations 6x faster after incidents.
What is Comprehensive Device Protection in 2025?

Device protection in 2025 extends far beyond simple antivirus software or a protective case. It’s a holistic approach that integrates physical security, cybersecurity, insurance coverage, policy enforcement, and continuous monitoring into a unified defense strategy. Think of it as a security ecosystem where each component reinforces the others.
At its core, modern device protection addresses three critical dimensions: prevention (stopping threats before they occur), detection (identifying threats in real-time), and recovery (restoring operations quickly after incidents). According to McKinsey’s 2025 Cybersecurity Report, organizations that implement all three dimensions experience 73% fewer successful attacks and recover 6.2 times faster when breaches do occur.
Device Protection: Then vs. Now
| Aspect | Traditional Approach (Pre-2020) | Modern Approach (2025) |
|---|---|---|
| Primary Focus | Antivirus and physical cases | Multi-layered security ecosystem with AI monitoring |
| Threat Model | Known viruses and physical damage | Zero-day exploits, AI-powered attacks, supply chain risks |
| Coverage | Desktop computers primarily | All endpoints: mobile, IoT, cloud, edge devices |
| Response Time | Hours to days | Real-time with automated responses |
| Insurance | Optional, rarely purchased | Essential component with cyber liability |
| User Role | Minimal awareness required | Active participants in security culture |
❓ Question for You: How many different types of devices does your business currently use on a daily basis? Have you inventoried them all for security purposes?
Why Device Protection Matters More Than Ever in 2025
The Business Impact: By the Numbers
The financial implications of inadequate device protection are staggering. Ponemon Institute’s 2025 Cost of Cyber Crime Study reveals that small businesses face average losses of $200,000 per successful cyberattack, with 60% of affected companies closing within six months of a major breach.
Consider these compelling statistics:
- Ransomware Evolution: Ransomware attacks on small businesses increased 105% in 2024-2025, with average ransom demands reaching $220,000.
- Mobile Vulnerability: 75% of successful breaches now originate from mobile devices, yet only 35% of businesses have mobile device management (MDM) solutions deployed.
- IoT Risks: The average business now operates 17 IoT devices, each representing a potential entry point for attackers.
- Downtime Costs: According to Gartner, the average cost of IT downtime has reached $5,600 per minute for small businesses.
- Regulatory Penalties: GDPR, CCPA, and emerging 2025 regulations have resulted in over $3.2 billion in fines globally, with small businesses not exempt.
💡 Pro Tip: Calculate your business’s “digital asset value” by adding up the replacement cost of all devices, the value of data stored on them, potential revenue loss during downtime, and regulatory penalty exposure. This number typically shocks business owners into prioritizing protection—most underestimate it by 300-400%.
Consumer Trust and Brand Protection
Beyond direct financial losses, device security breaches erode customer trust. PwC’s 2025 Digital Trust Insights found that 87% of consumers would take their business elsewhere after a data breach, and 65% would never return. In an age where online reviews spread instantly, a single security incident can permanently damage your reputation.
“In 2025, device security is brand security,” notes Dr. Sarah Chen, cybersecurity researcher at MIT’s Computer Science and Artificial Intelligence Laboratory. “Customers increasingly view how you protect their data as a direct reflection of how much you value their business.”
Ethical and Legal Obligations
Business owners now carry significant ethical and legal responsibilities for protecting customer data stored on their devices. The FTC’s 2025 Safeguards Rule mandates that businesses of all sizes implement comprehensive information security programs, with violations resulting in substantial penalties and personal liability for business owners.
Types of Device Protection: A Comprehensive Framework
| Protection Type | Description | Best For | Common Pitfalls |
|---|---|---|---|
| Physical Protection | Mobile devices, point-of-sale systems, and field equipment | Coverage for theft, damage, loss, and malfunction | Focusing only on drops/scratches while ignoring theft prevention |
| Cybersecurity Software | Antivirus, EDR, firewalls, VPN, email filtering | All connected devices, especially those handling sensitive data | Set-and-forget mentality; software requires regular updates and monitoring |
| Device Insurance | High-value devices, mobile equipment used outside the office | Coverage for data breaches, business interruption, and legal costs | Not reading exclusions; many policies don’t cover negligence or certain damage types |
| Cyber Liability Insurance | Automated backups, disaster recovery planning, and redundancy | Any business handling customer data or dependent on digital operations | Assuming general business insurance covers cyber incidents (it rarely does) |
| Access Control & Identity Management | Multi-factor authentication, biometrics, zero-trust architecture | All business systems, especially those with remote access | Making authentication so cumbersome that employees find workarounds |
| Data Backup & Recovery | Automated backups, disaster recovery planning, redundancy | Critical for all businesses; prioritize by data importance | Never testing recovery procedures until an emergency occurs |
| Employee Training | Security awareness, phishing recognition, policy compliance | Essential for all organizations; humans remain the weakest link | Annual training only; security awareness must be continuous |
📊 Visual Suggestion:
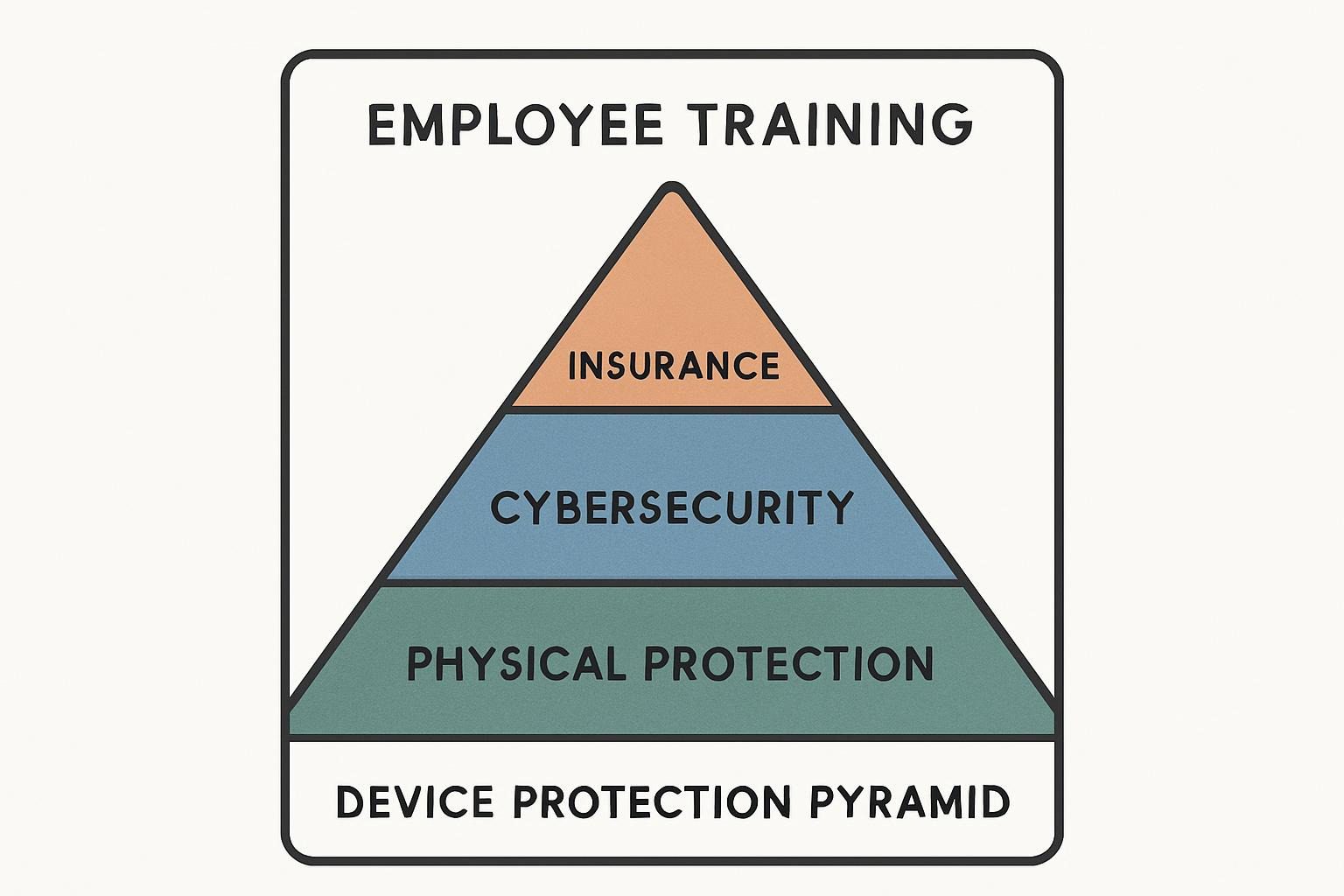
Essential Components of a Smart Device Protection Strategy
1. Endpoint Detection and Response (EDR)
Traditional antivirus is dead. In 2025, Forrester Research confirms that signature-based detection catches only 45% of threats. Modern EDR solutions use behavioral analysis and machine learning to identify anomalous activity in real-time.
Leading EDR platforms for small businesses include:
- CrowdStrike Falcon: Cloud-native, AI-powered threat detection with 99.5% prevention rate
- Microsoft Defender for Endpoint: Integrated with Microsoft 365, excellent for Windows-heavy environments
- SentinelOne: Autonomous response capabilities, particularly strong against ransomware
- Malwarebytes for Business: Cost-effective option for businesses with under 50 employees
⚡ Quick Hack: Enable EDR’s “rollback” feature, which can automatically undo changes made by malware. This single setting has saved businesses an average of 14 hours of recovery time per incident, according to recent studies.
2. Zero Trust Network Access (ZTNA)
The “castle and moat” security model is obsolete. Zero trust operates on the principle “never trust, always verify”—every access request is authenticated, authorized, and encrypted, regardless of where it originates.
Implementing zero trust involves:
- Multi-factor authentication (MFA) for all access
- Micro-segmentation of networks
- Least-privilege access controls
- Continuous monitoring and validation
- Device health verification before access
NIST’s Zero Trust Architecture framework provides excellent implementation guidance for businesses of all sizes.
3. Mobile Device Management (MDM)
With smartphones and tablets becoming primary work devices, MDM is no longer optional. These platforms allow you to enforce security policies, remotely wipe lost devices, control app installations, and monitor for compromised devices.
Top MDM solutions for 2025:
- Microsoft Intune: Seamless integration with the Microsoft ecosystem
- Jamf: The gold standard for Apple device management
- VMware Workspace ONE: Comprehensive multi-platform solution
- Hexnode: Budget-friendly option with robust features
❓ Question for You: If an employee’s smartphone with access to your business systems was stolen right now, how quickly could you remotely wipe it and revoke access?
4. Comprehensive Insurance Coverage
Insurance represents the financial safety net when prevention and detection fail. Modern device protection requires two distinct types of coverage:
Device Insurance: Covers physical damage, theft, and loss. Look for policies with:
- Replacement value coverage, not actual cash value
- Low or no deductibles
- Worldwide coverage for mobile devices
- Fast replacement (same-day or next-day)
- Coverage for accessories and peripherals
Cyber Liability Insurance: Covers data breaches, business interruption, and related costs. Essential coverage includes:
- First-party coverage (your direct losses)
- Third-party coverage (claims from customers/partners)
- Breach response costs (forensics, notification, credit monitoring)
- Business interruption and extra expenses
- Cyber extortion and ransomware payments
- Regulatory fines and penalties (where insurable)
According to insurance industry data, cyber liability premiums have increased 92% since 2023, but remain remarkably affordable for businesses with good security practices—often $1,500-$3,500 annually for $1 million in coverage.
🛡️ Protect Your Business Today
Get a free device protection assessment and customized insurance quote in under 10 minutes.Get Your Free Assessment
5. Automated Backup Systems
The 3-2-1 backup rule remains golden in 2025: 3 copies of your data, on 2 different media types, with 1 copy offsite. However, modern implementations add a fourth element: 1 copy offline (air-gapped) to protect against ransomware.
Cloud backup services have matured significantly. Leading options include:
- Backblaze for Business: Unlimited backup at flat pricing, excellent for large data volumes
- Acronis Cyber Protect: Combines backup with anti-malware and disaster recovery
- Carbonite: Simple, reliable, with strong customer support
- Veeam: Enterprise-grade features now accessible to small businesses
💡 Pro Tip: Schedule quarterly “fire drills” where you actually restore data from backups and measure how long it takes. Most businesses discover their backup systems don’t work as expected only during actual emergencies. The average first-time restore takes 3-4 times longer than anticipated.
6. Email Security Gateways
Email remains the #1 attack vector in 2025, with Proofpoint reporting that 94% of malware is delivered via email. Advanced email security goes beyond simple spam filtering to include:
- AI-powered phishing detection
- URL rewriting and sandboxing
- Attachment detonation
- Business email compromise (BEC) protection
- Data loss prevention (DLP)
Advanced Protection Strategies for 2025
AI-Powered Threat Hunting
The most sophisticated 2025 approach involves using AI to proactively hunt for threats rather than waiting for alerts. Security AI platforms analyze terabytes of data across all your devices and systems, identifying patterns that indicate potential compromises.
Darktrace pioneered this approach with “Cyber AI Analyst,” which performs the work of multiple security analysts 24/7. For small businesses, managed detection and response (MDR) services now offer similar capabilities at accessible price points ($200-800/month depending on device count).
⚡ Quick Hack: If full MDR is beyond your budget, implement CISA’s free threat intelligence feeds in your firewall and EDR platform. This governmental data stream warns of known bad actors and costs nothing beyond initial setup time.
Passwordless Authentication
Passwords are the weakest link in device security. In 2025, leading businesses are transitioning to passwordless authentication using FIDO2 security keys, biometrics, and device-based certificates.
Microsoft Entra ID (formerly Azure AD), Okta, and Duo Security offer passwordless solutions that reduce breach risk by 99.9% according to Microsoft’s internal data. Implementation costs have dropped to $3-8 per user per month, making this accessible even for small businesses.
Supply Chain Security
One emerging threat vector often overlooked: compromised hardware and software in the supply chain. The SolarWinds attack demonstrated how sophisticated actors can compromise thousands of businesses through a single vendor.
Protect your business by:
- Purchasing devices only from authorized resellers
- Verifying firmware integrity before deployment
- Maintaining a software bill of materials (SBOM) for all applications
- Segmenting networks to limit damage from compromised devices
- Requiring security attestations from vendors
Quantum-Resistant Encryption
While practical quantum computers remain 3-5 years away, “harvest now, decrypt later” attacks are already occurring. Forward-thinking businesses are beginning to implement NIST’s post-quantum cryptography standards to protect long-term sensitive data.
For most small businesses, ensuring your encryption solutions have quantum-ready upgrade paths is sufficient for now. Look for vendors committed to NIST’s PQC standards when purchasing new security tools.
📊 Visual Suggestion:
Real-World Case Studies: Device Protection in Action
Case Study 1: Regional Healthcare Provider Prevents $2.3M Ransomware Attack
Business: 150-employee healthcare clinic network in the Pacific Northwest
Challenge: Targeted by a sophisticated ransomware gang exploiting unpatched vulnerabilities in medical devices
Solution Implemented:
- Deployed CrowdStrike EDR across all endpoints, including IoT medical devices
- Implemented network segmentation, separating medical devices from administrative systems
- Enrolled in $3 $3M cyber liability policy with incident response retainer
- Established 3-2-1-1 backup protocol with daily testing
Result: EDR detected ransomware attempting lateral movement within 47 seconds and automatically isolated affected devices. Zero patient data was compromised, no ransom was paid, and operations continued without interruption. Total investment: $48,000 annually. Estimated loss prevented: $2.3 million plus irreparable reputation damage.
Key Takeaway: “The EDR paid for itself 40 times over in the first incident alone,” notes their IT director. “But more importantly, we maintained patient trust during a critical moment.”
Case Study 2: E-commerce Retailer Recovers from Hardware Failure in 90 Minutes
Business: $12M annual revenue online retailer specializing in handcrafted goods
Challenge: Primary server experienced a catastrophic hardware failure during the peak holiday shopping season
Solution Implemented:
- Veeam backup with hourly snapshots to cloud and local NAS
- Hot standby server provisioned through AWS
- Device insurance covering all critical hardware with same-day replacement
- Documented disaster recovery procedures are tested quarterly
Result: Business was fully operational within 90 minutes using hot standby. Lost only $3,200 in potential sales during the outage. Hardware insurance expedited replacement server delivery, which arrived next morning. Without this protection, estimated downtime would have been 4-6 days, costing approximately $180,000 in lost sales and customer acquisition.
Key Takeaway: Regular testing was crucial. “We knew exactly what to do because we’d done it before in drills,” the owner explained. “Muscle memory kicked in when panic wanted to take over.”
Case Study 3: Professional Services Firm Thwarts Business Email Compromise
Business: 35-person accounting and advisory firm
Challenge: Sophisticated phishing attack impersonating a senior partner to authorize a fraudulent wire transfer
Solution Implemented:
- Proofpoint email security with AI-powered BEC detection
- Mandatory monthly security awareness training with phishing simulations
- Multi-person approval process for all wire transfers over $10,000
- Passwordless authentication using YubiKey security keys
Result: Email security flagged the fraudulent request with a visible warning banner. Employee recognized the attempt due to recent training and reported it to IT. Investigation revealed the attacker had compromised a client’s email account (not the firm’s systems). The firm helped their client remediate the breach, strengthening the business relationship. Potential loss prevented: $87,500.
Key Takeaway: Human awareness remains critical. “Technology flagged it, but training ensured our employee knew what to do with that information,” their managing partner stated.
❓ Question for You: If you experienced a similar incident to these case studies, would your business survive? Do you have the protections and procedures in place to respond effectively?
Challenges, Limitations, and Ethical Considerations
Common Implementation Challenges
Employee Resistance: Security measures often create friction with daily workflows. The key is balancing security with usability. Harvard Business Review research shows that overly restrictive security policies lead to shadow IT and workarounds that actually decrease overall security.
Budget Constraints: Comprehensive protection requires investment. However, prioritization helps. Focus first on protecting your most critical assets and highest-risk areas, then expand coverage as budget allows. Many security tools offer free tiers suitable for very small businesses.
Technical Complexity: Not every business owner is tech-savvy. This is where managed security service providers (MSSPs) become valuable. For $500-2,000/month, MSSPs handle security operations, monitoring, and incident response—often cheaper than hiring in-house expertise.
False Sense of Security: Having tools doesn’t equal being protected. According to SANS Institute, 68% of businesses with security tools don’t properly configure them, leaving significant gaps. Professional setup and ongoing management are essential.
Limitations to Acknowledge
No security is perfect. Even with comprehensive protection:
- Zero-day vulnerabilities exist in all software and may be exploited before patches are available
- Insider threats from malicious or negligent employees can bypass many protections
- Sophisticated nation-state actors can potentially breach any system given enough time and resources
- Physical access to devices can often circumvent digital protections
- Social engineering remains highly effective despite technical controls
The goal isn’t perfect security (impossible) but rather risk reduction to acceptable levels while maintaining business functionality.
Ethical Considerations and Privacy
Device protection, especially monitoring and MDM solutions, raises important privacy questions:
Employee Privacy: Monitoring employee devices, emails, and activity must be balanced against privacy rights. Best practices include:
- Clear, written policies about what is and isn’t monitored
- Separate business and personal devices where possible
- Limiting monitoring to business-owned devices and business hours
- Transparency about monitoring capabilities
- Compliance with local privacy laws (GDPR, CCPA, etc.)
Customer Data: Your device protection directly impacts customer privacy. FTC guidelines emphasize that businesses must protect customer data with the same vigor as their own assets. Inadequate protection isn’t just a business risk—it’s an ethical failure to customers who trust you with their information.
Security vs. Accessibility: Overly restrictive security can exclude people with disabilities. Ensure your security measures accommodate assistive technologies and provide alternative authentication methods where biometrics may not work.
💡 Pro Tip: Create a “Security Ethics Committee” even in small businesses—just 2-3 people who periodically review your security practices for privacy implications, employee impact, and customer trust. This simple step prevents many problems before they occur and demonstrates good corporate citizenship.
The Risk of Security Theater
Be wary of “security theater”—measures that look impressive but provide minimal actual protection. Common examples include:
- Password complexity requirements without MFA (hackers rarely guess passwords; they steal them)
- Annual security training instead of continuous awareness
- Focusing on perimeter security while ignoring insider threats
- Compliance checkboxes without understanding the underlying risks
As security expert Bruce Schneier notes, “Security is a process, not a product.” Focus on systematic risk reduction rather than impressive-sounding features.
Future Trends: What’s Next for Device Protection (2025-2026)
AI-Driven Autonomous Defense
By late 2025 and into 2026, AI security systems will increasingly operate autonomously, making defensive decisions without human intervention. Gartner predicts that by 2027, 65% of security operations will be fully automated, freeing human analysts to focus on strategy and complex investigations.
This includes AI systems that automatically:
- Patch vulnerabilities based on threat intelligence
- Adjust security policies in response to new attack patterns
- Isolate compromised devices before humans detect the breach
- Generate and deploy custom security rules
Unified Security Platforms
The trend toward consolidation continues. Rather than juggling 10+ security tools, businesses are moving to unified platforms that integrate EDR, ZTNA, cloud security, email protection, and more under a single pane of glass.
Leading platforms to watch:
Microsoft Security (leveraging their ecosystem dominance), Palo Alto Prisma (comprehensive SASE), CrowdStrike Falcon (expanding beyond EDR), and Cisco SecureX (integration across networking and security).
Security-as-a-Service (SECaaS) Maturation
Small businesses will increasingly access enterprise-grade security through service models. Expect more sophisticated offerings at lower price points as providers achieve economies of scale. Markets and Markets projects the SECaaS market will reach $45.3 billion by 2027, with small business adoption accelerating.
Regulatory Expansion
Expect new regulations requiring minimum security standards for businesses of all sizes. The EU’s proposed Cyber Resilience Act will mandate security features for all connected devices, while similar legislation is emerging in California, New York, and other states. Non-compliance will carry significant penalties.
Biometric Everything
Passwords continue their decline. By 2026, expect behavioral biometrics (how you type, move your mouse, hold your phone) to supplement or replace traditional authentication. This “invisible” security protects without user friction.
Quantum Computing Timeline Acceleration
Recent breakthroughs suggest practical quantum computers may arrive sooner than expected. IBM and Google are racing toward “quantum advantage” for cryptographic attacks. Businesses should begin quantum-ready planning now, not in 2-3 years as previously recommended.
❓ Question for You: Which of these emerging trends do you think will have the biggest impact on your business? Are you preparing for any of them today?
People Also Ask: Quick Answers to Common Questions
Q: How much should a small business budget for device protection?
Industry standards suggest 3-7% of IT budget for security, translating to approximately $200-500 per employee annually for comprehensive protection including software, insurance, and managed services. Businesses handling sensitive data should budget toward the higher end.
Q: Is cyber insurance really necessary for small businesses?
Yes. The average cyber incident costs small businesses $200,000, yet comprehensive cyber liability insurance costs $1,500-3,500 annually for most small businesses. It’s one of the highest ROI investments you can make, covering breach response, legal fees, business interruption, and regulatory fines.
Q: What’s the single most important security measure to implement first?
Multi-factor authentication (MFA) across all business systems. Microsoft data shows MFA prevents 99.9% of account compromise attacks. It’s relatively inexpensive, easy to implement, and provides immediate, substantial risk reduction. Start here before anything else.
Q: How often should I update my device protection strategy?
Conduct quarterly reviews of your security posture, with comprehensive annual assessments. The threat landscape evolves rapidly—strategies effective six months ago may have significant gaps today. Also review immediately after any security incident or major business change.
Q: Can I protect my business devices without a dedicated IT person?
Yes, through managed security service providers (MSSPs) and cloud-based security tools. Many solutions specifically target non-technical business owners with simple setup and ongoing management. Budget $500-2,000/month for professional management, significantly less than hiring full-time IT staff.
Q: What should I do immediately after discovering a device breach?
1) Isolate the affected device from your network immediately, 2) Document everything you observe, 3) Contact your cyber insurance provider and IT support/MSSP, 4) Do NOT pay any ransom without expert consultation, 5) Preserve forensic evidence. Having an incident response plan prepared beforehand is critical.
Detailed FAQ: Deep Dives into Complex Questions
Comprehensive Answers
Q: How do I choose between different EDR solutions?
Evaluate based on:
1) Detection rate (look for independent testing from AV-Comparatives or SE Labs),
2) False positive rate (high false positives create alert fatigue),
3) Ease of use (critical if you lack dedicated security staff),
4) Response capabilities (can it automatically contain threats?),
5) Integration with your existing tools, and
6) Cost, including licensing, implementation, and ongoing management. Request proof-of-concept trials from your top 2-3 choices before committing.
Q: Should I allow employees to use personal devices for work (BYOD)?
BYOD offers cost savings and employee satisfaction, but significantly increases security complexity. If you allow it: 1) Require MDM enrollment on any device accessing business data, 2) Implement containerization separating business and personal data, 3) Enforce strong device encryption and authentication, 4) Have clear policies about remote wiping in case of loss/termination, 5) Consider providing device stipends instead to encourage business-owned devices. For businesses handling regulated data (healthcare, finance), company-owned devices are strongly recommended.
Q: What’s the difference between device insurance and cyber liability insurance?
Device insurance covers physical loss, theft, and damage to specific hardware—similar to insuring a company vehicle.
Cyber liability insurance covers digital risks like data breaches, business interruption from cyberattacks, ransomware, and legal liability from compromised customer data. You need both: device insurance protects the hardware investment, while cyber liability protects your business operations and reputation. They’re complementary, not substitutes.
Q: How can I tell if my current device protection is adequate?
Conduct a security audit by asking: 1) When was your last security assessment? (should be within 12 months), 2) Do you have EDR on all endpoints? (not just antivirus), 3) Is MFA enforced everywhere? (no exceptions), 4) When did you last test your backup recovery? (should be quarterly), 5) Do you have cyber insurance? (critical safety net), 6) Have employees completed security training recently? (within 3 months). If you answered “no” or “unsure” to more than two questions, significant gaps exist. Consider hiring a security consultant for a professional assessment ($2,000-5,000 for small businesses, money well spent).
Essential Device Protection Checklist
| Category | Action Item | Priority | Estimated Cost |
|---|---|---|---|
| Immediate (Week 1) | Enable MFA on all business accounts | Critical | Free – $5/user/month |
| Immediate | Inventory all business devices and data | Critical | Time investment only |
| Immediate | Implement automatic security updates | Critical | Free (built into OS) |
| Month 1 | Establish a 3-2-1-1 backup system | High | $3-12/device/month |
| Month 1 | Create an incident response plan | High | $50-300/month |
| Month 1 | Purchase cyber liability insurance | High | $1,500-3,500/year |
| Month 2 | Implement advanced email security | High | $3-10/user/month |
| Month 2 | Deploy MDM for mobile devices | High | $4-10/device/month |
| Month 2 | Conduct employee security training | High | $20-50/employee (one-time) |
| Month 3 | Implement network segmentation | Medium | $500-2,000 (one-time) |
| Month 3 | Create incident response plan | Medium | Time or $1,000-2,500 consulting |
| Ongoing | Monthly security awareness reinforcement | Medium | Time investment |
| Ongoing | Quarterly backup recovery testing | Medium | Time investment |
| Ongoing | Annual security assessment | Medium | $2,000-5,000/year |
📊 Visual Suggestion:
Conclusion: Your Device Protection Action Plan
Device protection in 2025 is not optional—it’s fundamental to business survival and success. The threat landscape will only intensify as attackers leverage AI, quantum computing approaches the horizon, and the value of data continues to skyrocket. However, comprehensive protection is more accessible than ever for businesses of all sizes.
The businesses that thrive will be those that embrace security as a strategic advantage rather than viewing it as a cost center. Your customers increasingly choose vendors based on security practices. Your insurance premiums reflect your security posture. Your ability to weather incidents determines your longevity.
Here’s your action plan for the next 30 days:
- Week 1: Enable MFA everywhere and conduct a device/data inventory
- Week 2: Implement automated backups and test recovery
- Week 3: Deploy EDR to all endpoints and evaluate cyber insurance options
- Week 4: Conduct security training and create your incident response plan
These four steps alone will reduce your risk by an estimated 70-80% according to cybersecurity research. The remaining protection layers build on this foundation.
Remember: perfect security is impossible, but dramatic risk reduction is absolutely achievable with the right combination of technology, insurance, policies, and training. The question isn’t whether you can afford comprehensive device protection—it’s whether you can afford not to have it.
As cybersecurity expert Mikko Hyppönen wisely notes: “We’re going to see more cyberattacks, more cybercrime, more everything. The only way forward is to build better defenses.” Start building yours today.
🚀 Ready to Protect Your Business?
Get personalized device protection recommendations and a custom insurance quote tailored to your business needs. Our experts will analyze your current setup and identify gaps—completely free, no obligation.Start Your Free Security Assessment
Or call us at 1-800-INSURE-GO for immediate assistance
About the Author
Marcus Chen, CISSP, CISM, is a cybersecurity consultant and risk management specialist with 15 years of experience helping small and medium businesses implement comprehensive security programs. He holds master’s degrees in Computer Science and Business Administration from Stanford University and has consulted for over 200 businesses across retail, healthcare, professional services, and manufacturing sectors.
Marcus regularly speaks at industry conferences about practical, cost-effective security strategies for resource-constrained businesses. He founded SecureSmallBiz, a consultancy dedicated to democratizing enterprise-grade security for businesses of all sizes.
Expertise: Cybersecurity strategy, risk assessment, compliance, incident response, security architecture, and insurance optimization for small-to-medium enterprises.
Keywords
device protection 2025, small business cybersecurity, endpoint security solutions, cyber liability insurance, device insurance for businesses, ransomware protection, data breach prevention, zero trust security, multi-factor authentication, EDR solutions, mobile device management, business device security, cybersecurity best practices, small business IT security, device protection strategies, cyber insurance coverage, security awareness training, backup and disaster recovery, business continuity planning, network security for small business, IoT device security, cloud security, email security gateway, incident response planning, security compliance
Disclaimer: This article provides general information and guidance on device protection strategies. It should not be considered legal, financial, or professional advice. Security requirements vary by industry, jurisdiction, and business specifics. Consult with qualified cybersecurity professionals, legal advisors, and insurance specialists to develop a protection strategy appropriate for your specific circumstances. Product mentions and recommendations are for informational purposes only and do not constitute endorsements. All statistics and data cited are accurate as of the publication date but may change over time.
Last Updated: October 2025 | Next Review: January 2026
